Threat Detection and Response
Find and Stop the Most Harmful Attacks Before Damage is Done
Objective: Improved Threat Detection and Response
It is more critical than ever for organizations to detect, validate and contain threats very quickly. Unfortunately, today’s security tools and approaches are unable to stop all threats from penetrating the perimeter. Even worse is that they are unable to identify and respond to them as they spread throughout the network causing damage as they go. It is clear that a better approach is needed.

Purpose-built solutions to automatically identify, contain and remediate cyber threats
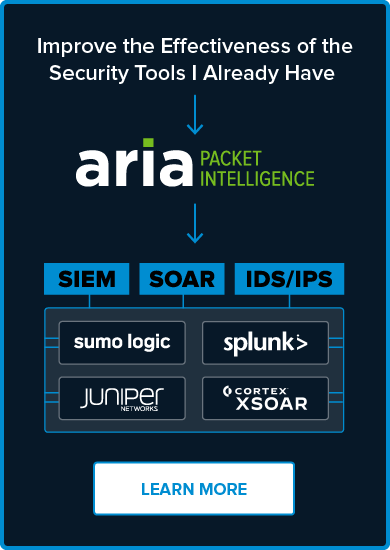
No matter your environment or level of cyber security maturity we have a solution to best suit your needs. Our ARIA ADR and ARIA PI solutions were developed from the ground up to help organizations address the challenges preventing effective threat detection and response. Now you can surgically contain threats without disrupting the business by taking infected devices or applications offline to remediate. Our solutions either help augment the security tools you have to cover IoT or provide a better, more cost-effective, fully automated and scalable solution for those looking for a new approach.
Full SOC capabilities at a fraction of the cost
Find and stop every threat type across on-premises and cloud environments as well as those posed by new employees working remotely
Achieve the quickest MTTD and MTTR, while reducing man hours to do so
Provide easy-to-read, validated alerts with automated containment using AI and ML
Artificial Intelligence (AI) and Machine Learning (ML)
Consolidate security spend, and save significant capital and operational expenses
Complete visibility for faster response and containment
Offers four configurations to meet a wide variety of network intelligence and cybersecurity requirements
Provides visibility into all network traffic by feeding analytics to packet delivery accounting tools and quality of service SLA monitoring applications
Performs full network monitoring of all critical assets and application data, including lateral traffic flow
Runs at wire-rate (10G or up to 25G) without impacting network or application performance
The Problem
Why the Need for a Better Approach to Threat Detection and Response?

Too Much Alert “Noise”
Every day, on average, an organization’s security stack of point solutions generates 5,000 alerts. It is impossible to investigate each one. To combat this, companies spend an exorbitant amount of time and money writing and updating filters to attempt to weed out false security alerts.

A Lack of Internal Network Visibility
Up to 80% of an organization’s threat surface goes unmonitored. This is the internal network and all traffic moving laterally—between devices, and between the public and private cloud instances. This creates sizable network visibility gaps and allows network-borne threats, like ransomware and malware, to move unseen in the network and doing great harm along the way.

Significant Investment with Little ROI
In an attempt to find and stop cyber threats companies must make significant investments in products, processes, and people. Yet, the best-of-breed and industry standard approach to threat detection still relies on separate processes to stop attacks. Quite often organizations settle for purchasing only the individual components they can afford and manage. As a result, they end up with very limited coverage.
Contact Us to Speak to a Cybersecurity Expert!
Resources and Related Content
Resources
Blog
News
ARIA Cybersecurity, a CSPi business (NASDAQ: CSPi) and a leading provider of cybersecurity solutions, announced a new contract via its new reseller partnership with…
Oryx Industries, a leading provider of trailblazing cybersecurity solutions, has announced a strategic partnership with ARIA Cybersecurity, a CSPi business (NASDAQ: CSPi), integrating the…
ARIA Cybersecurity, a CSPi business (NASDAQ: CSPi) and a leading provider of cybersecurity solutions, announced a new reseller partnership with Rexel USA, an industry…
Events